Vishing is a crime that consists of impersonating companies, calling the victim by phone and obtaining their data. Cybercriminals can gain remote access to your computer if you follow their instructions.
“They called me and I ended up sending money to a scammer”
Definition:
Vishing is the fraudulent practice of making phone calls or leaving voice messages purporting to be from reputable companies in order to induce individuals to reveal personal information or download malware that could compromise personal information in their computer.
The attacker usually ask that a victim perform one or all of the following:
- Follow a link, either to download a file or to submit some information
- Provide answer or reply to a message with personal or sensitive information
- Carry out an action such as transfer funds or purchase coupons
Here, the attacker uses impersonation to exploit the target’s trust and unfortunately, the change and uncertainty brought about by the COVID-19 pandemic have exacerbated this problem.
Vishing Attack
Despite having the most sophisticated technology at their disposal, cybercriminals often resort to methods that are technically archaic, such as making phone calls.
Check out this example: A user receives a call from a suspected Microsoft technician warning him that his computer has a virus and that he must follow his recommendations in order to solve it.
The alleged specialist tells him that he must download a remote control application so that he can help him manage the incident from his office.
And so, starting from a more or less common problem and, without a doubt, alarming, such as malware on the personal computer, cybercriminals manage to gain unlimited access to the victim’s computer and, with that, to all the information stored on it.

Be careful: if they call you from a supposed anti-fraud department of the bank, they want to scam you
An assumption like this could open the door to another series of crimes, such as the theft of documentation and personal information, bank credentials and even the purchase of cryptocurrencies.
If you have the typical folder with the scanned ID or other important documentation, they could charge you, sign you up for services without your consent, and you could be the victim of more fraud in your name or even extortion.
Although it is true that many Vishing victims begin to notice strange things along the way, and decides not to follow the instructions, many others end up being victims as they believe that it is really a technician that is dealing with them.
In these cases, it is essential to take action as soon as possible.
”I just fell victim to a vishing call and sent money to a scammer. I have already filed a complaint with the police. Do you have any kind of insurance against this? Can I do something else?” This is the questions made by a Twitter user , just after becoming victim of vishing.
He is not the only one to share his experience through this network. Another user who warned her followers of the scam told a journalist that, although she did not comply to the vishing attack, she received a call in which she was asked for a code that had supposedly been sent to her mobile phone, which could have given them access to her bank account.
What is smishing and vishing?

Smishing and vishing are types of phishing attacks that utilizes email, text messaging or voice calls techniques to manipulate targeted victims into giving over sensitive information to criminals that operate on the cyber realm.
It is not uncommon for cybercriminals to falsify or design their numbers or emails so that the company’s client and potential victim will think they are actually from their company.
Although the phone number appears to be correct, they have been able to falsify it or divert it to another number. The same happens with emails and text messages. This makes it difficult for the user to know at first that it is a scam, a potential vishing attack.
In most cases, the payments that are requested are very small, since, if you are the victim of a charge of $3 or three euros, for example, it is more difficult to suspect and report it.
They do it precisely “so as not to arouse suspicion, and it is easier for a user to fall for a scam like this than for a large one, where the alarms go off more easily.
To most smart and patient criminals that operate through vishing attack, it is less risky, and more profitable to deceive, for example, a million users who pay two euros, than a few for more money.
You Might Be Interested in: An Easy Guide To Understanding Auto money Title Loans in 7 Minutes
How to prevent vishing
If you do fall for a vishing attack, it’s important to surf and search the internet for yourself to see if there is any of your personal data that is on a websites where it shouldn’t be.
In the event that you have been tricked to install remote control tools that allow the cybercriminal to access your computer, the first thing they should do is uninstall it, disconnect the device from the internet as soon as possible and carry out an antivirus scan and cleaning process to eliminate files that could continue to send information to the attacker.
The impersonation of trusted companies or entities to obtain personal data through a simple call is still a very common scam attempt these days. One of the most common strategies is to impersonate a technical support member of a government agency or a technology company like Microsoft.
Every month, Microsoft receives some 6,500 incidents globally, of vishing attack, although in previous years it could reach 13,000 .
This is due to the fact that “the potential victims who uses windows OS are so much more than those that can be found among Linux or iOS users. Almost 89% of PC users in the world have Windows operating system installed , compared to 8.5% with iOS and less than 2% with Linux.
There is a rebound in vishing cases in recent weeks.
According to the head of the Criminal Cyber Intelligence Group of the Judicial Police Technical Unit of the Civil Guard, there have been cases of quite active campaigns.
There are more cases for a few months and then there is a quieter period. But unfortunately, they are quite frequent. Among the companies most prone to being impersonated, in addition to technology companies such as Microsoft, are banks .
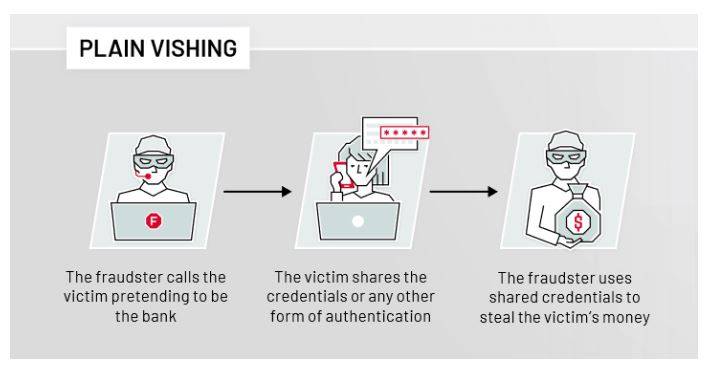
Most of the time, these scams are hatched through organized criminal syndicates. These are groups that have telemarketers who open the first door.
This group performs a first filtering and, once they see that they can hook the victim, they transfer calls to higher quality scammers, who have technical knowledge and invite them to install the software that expose victim’s computer to be remote controlled.
Another part of the criminal organization is in charge of managing the data that is stolen or the payments. There are many people behind it who are organized in different branches.
Although it is not the most common, cybercriminals can search for information about the victim on the Internet to better orchestrate the scam.
This is very useful if, for example, you want to commit fraud on behalf of a bank and the user has contracted a service with that bank because, if you are not a customer or user, it is more complicated for you to end up being a victim of the vishing attack.
In general, they don’t look for specific people, but they get access to a bag of data and start calling.
The thing to keep in mind when receiving a call from a supposed company, especially if you happen to be a customer of that company, is to determine if you were expecting a call. If you don’t expect it, be suspicious.
The things that should generate or arouse suspicion include:
- If you are a client of the alleged company, but they tell you information that is strange to you or you do not understand well, it is best to cut off communication and go directly to the official contacts of the company.
- If you cannot hear well, there is a lot of background noise or it seems that the other person is not understanding you, if the communication is cut off or they do not know how to answer the questions you ask, be suspicious. Sometimes they don’t answer or just hang up.
- If you are asked to provide any personal information that a company of which you are a customer should know.
- And we can also be suspicious if they send you to install something, no matter what the pretext is. But above all, common sense should be used.
Interestingly, according to Microsoft, it is people between the ages 18-37) who are the most exposed to tech support scams , due to overestimating their skills regarding the use of computers and the Internet.
The company calculates that 59% (global average) of adults have been exposed to a vishing attack or scam of this type in the past year.






